 UPDATE (10-20-2008): 4.01 m33-2 is NO LONGER the latest hacked PSP Firmware. The newest one is 5.00 M33-3 and can be found HERE - How to hack the PSP.
So if you just bought a PSP and want to get into custom firmware, this is the right place to be. If you already have custom firmware on your PSP and just want to upgrade to 4.01, skip below to the 4.01 section. Update: This works on the new blue Madden PSP as well!
Requirements:
1. PSP Pandora Battery
2. Memory Stick Pro Duo (64mb to 8gb TESTED so far - any will do).
3. psp-grader-v005-lite-setup
4. Official PSP 3.90 Firmware.
Steps:
1. Install PSP Grader on your computer.
2. Run PSP Grader and select the location of the 3.90 firmware and drive for your memory stick
3. Hit run and let the program create a “Magic Memory Stick” for you.
4. Your Memory stick is now ready, insert the Pandora’s Battery whilst holding the L should button on the PSP. Once the IPL has loaded on the PSP simply press the X button. Wait. After around 1 - 3 minutes the Flash shall be done, press X to shutdown the psp, it is now safe to remove the pandora battery. Its is very important to just wait and not switch off the PSP or remove the Memory Stick or Pandora’s Battery, it could result in a brick if you do not wait.
5. Once that is done, you can format the memory stick with your psp to use to load games. Games are normally loaded in the “ISO” folder. you need to hit select on the PSP to get the ISO mode correct. Use the “Sony NP9660″ one.
This was the easiest way I could find to get the PSP to 3.90 m33-3, from there you are going to just run two more updates to reach 4.01-m33-2
Steps to finish the hack to Version 4.01….
If you already have custom firmware you can skip the steps above and jump directly here.
1. Download the following files:.
a. 401-m33 (Hacked firmware v4.01 m33-1)
b. 401m332 (Hacked firmware v4.01 m33-2)
c. Offical PSP 4.01 Firmware.
2. Extract the 401-m33 files and the official 4.01 firmware update. Rename the 4.01 official update to 401.PBP and then copy it to the 401-m33’s extracted UPDATE folder.
3. Copy the UPDATE folder to the memory stick on your psp to the following location: “/PSP/GAME/”
4. In your PSP go to Games, and then run the update. This will take your PSP to version 4.01 m33-1
5. Delete the UPDATE folder you just created in “/PSP/GAME/”.
6. Extract the 401m332 file and copy the extracted UPDATE folder to your PSP memory stick under “/PSP/GAME/”
7. In your PSP go to Games, and then run the update.
That’s it. You are all patched up to the latest version of the time of this posting!
There is also an add-on pack to this firmware that gives the PSP additional features like Screenshots, video capture, etc.
That can be found here:
How to take Screen Shots of PSP Games and More
Also if you are looking for a jump start to getting emulators to run on your PSP, you should check out:
Capcom CPS2 Emulator for the PSP Slim and also
Capcom CPS1 Emulator for the PSP Slim. Those two articles should atleast get you on your feet.
Images/Code Retard
UPDATE (10-20-2008): 4.01 m33-2 is NO LONGER the latest hacked PSP Firmware. The newest one is 5.00 M33-3 and can be found HERE - How to hack the PSP.
So if you just bought a PSP and want to get into custom firmware, this is the right place to be. If you already have custom firmware on your PSP and just want to upgrade to 4.01, skip below to the 4.01 section. Update: This works on the new blue Madden PSP as well!
Requirements:
1. PSP Pandora Battery
2. Memory Stick Pro Duo (64mb to 8gb TESTED so far - any will do).
3. psp-grader-v005-lite-setup
4. Official PSP 3.90 Firmware.
Steps:
1. Install PSP Grader on your computer.
2. Run PSP Grader and select the location of the 3.90 firmware and drive for your memory stick
3. Hit run and let the program create a “Magic Memory Stick” for you.
4. Your Memory stick is now ready, insert the Pandora’s Battery whilst holding the L should button on the PSP. Once the IPL has loaded on the PSP simply press the X button. Wait. After around 1 - 3 minutes the Flash shall be done, press X to shutdown the psp, it is now safe to remove the pandora battery. Its is very important to just wait and not switch off the PSP or remove the Memory Stick or Pandora’s Battery, it could result in a brick if you do not wait.
5. Once that is done, you can format the memory stick with your psp to use to load games. Games are normally loaded in the “ISO” folder. you need to hit select on the PSP to get the ISO mode correct. Use the “Sony NP9660″ one.
This was the easiest way I could find to get the PSP to 3.90 m33-3, from there you are going to just run two more updates to reach 4.01-m33-2
Steps to finish the hack to Version 4.01….
If you already have custom firmware you can skip the steps above and jump directly here.
1. Download the following files:.
a. 401-m33 (Hacked firmware v4.01 m33-1)
b. 401m332 (Hacked firmware v4.01 m33-2)
c. Offical PSP 4.01 Firmware.
2. Extract the 401-m33 files and the official 4.01 firmware update. Rename the 4.01 official update to 401.PBP and then copy it to the 401-m33’s extracted UPDATE folder.
3. Copy the UPDATE folder to the memory stick on your psp to the following location: “/PSP/GAME/”
4. In your PSP go to Games, and then run the update. This will take your PSP to version 4.01 m33-1
5. Delete the UPDATE folder you just created in “/PSP/GAME/”.
6. Extract the 401m332 file and copy the extracted UPDATE folder to your PSP memory stick under “/PSP/GAME/”
7. In your PSP go to Games, and then run the update.
That’s it. You are all patched up to the latest version of the time of this posting!
There is also an add-on pack to this firmware that gives the PSP additional features like Screenshots, video capture, etc.
That can be found here:
How to take Screen Shots of PSP Games and More
Also if you are looking for a jump start to getting emulators to run on your PSP, you should check out:
Capcom CPS2 Emulator for the PSP Slim and also
Capcom CPS1 Emulator for the PSP Slim. Those two articles should atleast get you on your feet.
Images/Code Retard
Saturday, May 16, 2009
How to Hack your PSP to 4.01 M33-2 (The Easy Way)
 UPDATE (10-20-2008): 4.01 m33-2 is NO LONGER the latest hacked PSP Firmware. The newest one is 5.00 M33-3 and can be found HERE - How to hack the PSP.
So if you just bought a PSP and want to get into custom firmware, this is the right place to be. If you already have custom firmware on your PSP and just want to upgrade to 4.01, skip below to the 4.01 section. Update: This works on the new blue Madden PSP as well!
Requirements:
1. PSP Pandora Battery
2. Memory Stick Pro Duo (64mb to 8gb TESTED so far - any will do).
3. psp-grader-v005-lite-setup
4. Official PSP 3.90 Firmware.
Steps:
1. Install PSP Grader on your computer.
2. Run PSP Grader and select the location of the 3.90 firmware and drive for your memory stick
3. Hit run and let the program create a “Magic Memory Stick” for you.
4. Your Memory stick is now ready, insert the Pandora’s Battery whilst holding the L should button on the PSP. Once the IPL has loaded on the PSP simply press the X button. Wait. After around 1 - 3 minutes the Flash shall be done, press X to shutdown the psp, it is now safe to remove the pandora battery. Its is very important to just wait and not switch off the PSP or remove the Memory Stick or Pandora’s Battery, it could result in a brick if you do not wait.
5. Once that is done, you can format the memory stick with your psp to use to load games. Games are normally loaded in the “ISO” folder. you need to hit select on the PSP to get the ISO mode correct. Use the “Sony NP9660″ one.
This was the easiest way I could find to get the PSP to 3.90 m33-3, from there you are going to just run two more updates to reach 4.01-m33-2
Steps to finish the hack to Version 4.01….
If you already have custom firmware you can skip the steps above and jump directly here.
1. Download the following files:.
a. 401-m33 (Hacked firmware v4.01 m33-1)
b. 401m332 (Hacked firmware v4.01 m33-2)
c. Offical PSP 4.01 Firmware.
2. Extract the 401-m33 files and the official 4.01 firmware update. Rename the 4.01 official update to 401.PBP and then copy it to the 401-m33’s extracted UPDATE folder.
3. Copy the UPDATE folder to the memory stick on your psp to the following location: “/PSP/GAME/”
4. In your PSP go to Games, and then run the update. This will take your PSP to version 4.01 m33-1
5. Delete the UPDATE folder you just created in “/PSP/GAME/”.
6. Extract the 401m332 file and copy the extracted UPDATE folder to your PSP memory stick under “/PSP/GAME/”
7. In your PSP go to Games, and then run the update.
That’s it. You are all patched up to the latest version of the time of this posting!
There is also an add-on pack to this firmware that gives the PSP additional features like Screenshots, video capture, etc.
That can be found here:
How to take Screen Shots of PSP Games and More
Also if you are looking for a jump start to getting emulators to run on your PSP, you should check out:
Capcom CPS2 Emulator for the PSP Slim and also
Capcom CPS1 Emulator for the PSP Slim. Those two articles should atleast get you on your feet.
Images/Code Retard
UPDATE (10-20-2008): 4.01 m33-2 is NO LONGER the latest hacked PSP Firmware. The newest one is 5.00 M33-3 and can be found HERE - How to hack the PSP.
So if you just bought a PSP and want to get into custom firmware, this is the right place to be. If you already have custom firmware on your PSP and just want to upgrade to 4.01, skip below to the 4.01 section. Update: This works on the new blue Madden PSP as well!
Requirements:
1. PSP Pandora Battery
2. Memory Stick Pro Duo (64mb to 8gb TESTED so far - any will do).
3. psp-grader-v005-lite-setup
4. Official PSP 3.90 Firmware.
Steps:
1. Install PSP Grader on your computer.
2. Run PSP Grader and select the location of the 3.90 firmware and drive for your memory stick
3. Hit run and let the program create a “Magic Memory Stick” for you.
4. Your Memory stick is now ready, insert the Pandora’s Battery whilst holding the L should button on the PSP. Once the IPL has loaded on the PSP simply press the X button. Wait. After around 1 - 3 minutes the Flash shall be done, press X to shutdown the psp, it is now safe to remove the pandora battery. Its is very important to just wait and not switch off the PSP or remove the Memory Stick or Pandora’s Battery, it could result in a brick if you do not wait.
5. Once that is done, you can format the memory stick with your psp to use to load games. Games are normally loaded in the “ISO” folder. you need to hit select on the PSP to get the ISO mode correct. Use the “Sony NP9660″ one.
This was the easiest way I could find to get the PSP to 3.90 m33-3, from there you are going to just run two more updates to reach 4.01-m33-2
Steps to finish the hack to Version 4.01….
If you already have custom firmware you can skip the steps above and jump directly here.
1. Download the following files:.
a. 401-m33 (Hacked firmware v4.01 m33-1)
b. 401m332 (Hacked firmware v4.01 m33-2)
c. Offical PSP 4.01 Firmware.
2. Extract the 401-m33 files and the official 4.01 firmware update. Rename the 4.01 official update to 401.PBP and then copy it to the 401-m33’s extracted UPDATE folder.
3. Copy the UPDATE folder to the memory stick on your psp to the following location: “/PSP/GAME/”
4. In your PSP go to Games, and then run the update. This will take your PSP to version 4.01 m33-1
5. Delete the UPDATE folder you just created in “/PSP/GAME/”.
6. Extract the 401m332 file and copy the extracted UPDATE folder to your PSP memory stick under “/PSP/GAME/”
7. In your PSP go to Games, and then run the update.
That’s it. You are all patched up to the latest version of the time of this posting!
There is also an add-on pack to this firmware that gives the PSP additional features like Screenshots, video capture, etc.
That can be found here:
How to take Screen Shots of PSP Games and More
Also if you are looking for a jump start to getting emulators to run on your PSP, you should check out:
Capcom CPS2 Emulator for the PSP Slim and also
Capcom CPS1 Emulator for the PSP Slim. Those two articles should atleast get you on your feet.
Images/Code Retard
How to Download free MP3’s from using Google
Free Apple iPhone App Store Apps of the Day - 5/15/09
 Get them now while they’re hot! These iPhone apps have been recently reduced to the recession friendly price of free! There’s no word when these app prices will shoot back up (usually these freebies are only good for a couple of days as app publishers try to get a little publicity) so make no delay and point your iTunes to the App Store and get to downloading!
* Eric Thayne’s Eggs Away!: Accelerometer-based balancing game
* Laminar Research’s X-Plane-Trainer: Flight simulation training
* Aaron Marlin’s Trash Day: Trash pickup reminders
* InnerFour’s iCopter 3D: FREE: Acceleromterer-based flight simulator
* noidentity’s RadioAlarm: Internet radio alarm clock
* ustwo’s Steppin: Touchscreen-based balance game
* Peter Damen’s Pitch & Roll: Inclinometer
Get them now while they’re hot! These iPhone apps have been recently reduced to the recession friendly price of free! There’s no word when these app prices will shoot back up (usually these freebies are only good for a couple of days as app publishers try to get a little publicity) so make no delay and point your iTunes to the App Store and get to downloading!
* Eric Thayne’s Eggs Away!: Accelerometer-based balancing game
* Laminar Research’s X-Plane-Trainer: Flight simulation training
* Aaron Marlin’s Trash Day: Trash pickup reminders
* InnerFour’s iCopter 3D: FREE: Acceleromterer-based flight simulator
* noidentity’s RadioAlarm: Internet radio alarm clock
* ustwo’s Steppin: Touchscreen-based balance game
* Peter Damen’s Pitch & Roll: Inclinometer
Saturday, May 2, 2009
How-to: using the new Facebook stream API in a desktop app
Number of confirmed H1N1 cases worldwide soars
Freedom of the media declines worldwide, report says
 "Global declines in press freedom" persisted last year, with setbacks highlighted in Israel, Italy, Taiwan, Hong Kong and elsewhere across the world, an annual survey said Friday.
Media freedom campaigners don gags during a news conference in Hong Kong in April 2008.
Media freedom campaigners don gags during a news conference in Hong Kong in April 2008.
Freedom House, a nongovernmental organization that supports democracy and freedom of the media, said in its annual press freedom survey that "negative trends" outweighed "positive movements in every region, particularly in the former Soviet Union, the Middle East and North Africa."
"This marked the seventh straight year of overall deterioration. Improvements in a small number of countries -- including bright spots in parts of South Asia and Africa -- were overshadowed by a continued, relentless assault on independent news media by a wide range of actions, in both authoritarian states and countries with very open media environments."
Israel -- once the only country to be consistently rated free by the group in the Middle East and North Africa -- was ranked as "partly free" because of the Gaza conflict.
The report cited "increased travel restrictions on both Israeli and foreign reporters; official attempts to influence media coverage of the conflict within Israel; and greater self-censorship and biased reporting, particularly during the outbreak of open war in late December."
Elsewhere in the Middle East, there are concerns about harassment of journalists and bloggers in Libya, Iran, Syria, Tunisia and Saudi Arabia. The drop in violence in war-torn Iraq helped journalists move around the country, and a new law in the Kurdish region gave journalists "unprecedented freedoms."
Hong Kong, which is part of China, also dropped in rankings from free to partly free, a reflection of "the growing influence of Beijing over media and free expression in the territory."
Don't Miss
* Journalist jailed in Iran may seek pardon
* U.S. journalists to be tried in North Korea
* Journalists freed in Azerbaijan
* Read the report (PDF)
"Of particular concern were the appointment of 10 owners of Hong Kong media outlets to a mainland Chinese political advisory body, increased restrictions on film releases in the period surrounding the Olympics, and reports that critics of Beijing encountered growing difficulty in gaining access to Hong Kong media platforms."
The report cited deterioration of of freedoms in Taiwan, which has been characterized as East Asia's freest media environment. That's because of "legal pressures and attempts to control broadcast media outlets."
Italy dropped from free to partly free because of the "increased use of courts and libel laws to limit free speech, heightened physical and extralegal intimidation by both organized crime and far-right groups, and concerns over media ownership and influence," the report said.
It cited fears about media magnate Silvio Berlusconi becoming prime minister again. There are concerns about "the concentration of state-owned and private outlets under a single leader."
In the former Soviet Union, "legal pressure and attempts to control broadcast media outlets" were cited in Russia, Armenia and Kyrgyzstan. The report noted other problems in Russia, saying "reporters suffer from a high level of personal insecurity, and impunity for past murders or physical attacks against journalists is the norm."
Across Africa, there were "some improvements," citing developments in Comoros, Sierra Leone, Angola, and Liberia. But there were continued problems in places like Zimbabwe and Eritrea.
"Senegal took a significant step backward due to a dramatic increase in both legal and extralegal action against journalists and media houses, accompanied by overtly hostile rhetoric from the president and other officials," the report said.
The report cited strides in South Asian nations, ranking the once "not free" Maldives to "partly free." It mentioned a "new constitution protecting freedom of expression, the opening of additional private radio and television stations, the release of a prominent journalist from life imprisonment, and a general loosening of restrictions after the country's first democratic presidential election in October."
It said Bangladesh and Pakistan reversed declines in freedom of the media. But there were setbacks in Afghanistan and Sri Lanka, two countries racked by warfare.
In some countries in the Americas, such as Mexico, Bolivia and Ecuador, "attacks and official rhetoric against the media escalated." Venezuela and Cuba were ranked as not free, and there were "high levels of intimidation and self-censorship" in Colombia and Guatemala. Positive developments were noted in Guyana, Haiti and Uruguay.
The worst-rated countries in the world are Myanmar, Cuba, Eritrea, Libya, North Korea and Turkmenistan.
"Given the current economic climate, which is certain to place a further strain on media sustainability and diversity in rich and poor countries alike, pressures on media freedom are now looming from all angles and are increasingly threatening the considerable gains of the past quarter-century," the report said.
"Global declines in press freedom" persisted last year, with setbacks highlighted in Israel, Italy, Taiwan, Hong Kong and elsewhere across the world, an annual survey said Friday.
Media freedom campaigners don gags during a news conference in Hong Kong in April 2008.
Media freedom campaigners don gags during a news conference in Hong Kong in April 2008.
Freedom House, a nongovernmental organization that supports democracy and freedom of the media, said in its annual press freedom survey that "negative trends" outweighed "positive movements in every region, particularly in the former Soviet Union, the Middle East and North Africa."
"This marked the seventh straight year of overall deterioration. Improvements in a small number of countries -- including bright spots in parts of South Asia and Africa -- were overshadowed by a continued, relentless assault on independent news media by a wide range of actions, in both authoritarian states and countries with very open media environments."
Israel -- once the only country to be consistently rated free by the group in the Middle East and North Africa -- was ranked as "partly free" because of the Gaza conflict.
The report cited "increased travel restrictions on both Israeli and foreign reporters; official attempts to influence media coverage of the conflict within Israel; and greater self-censorship and biased reporting, particularly during the outbreak of open war in late December."
Elsewhere in the Middle East, there are concerns about harassment of journalists and bloggers in Libya, Iran, Syria, Tunisia and Saudi Arabia. The drop in violence in war-torn Iraq helped journalists move around the country, and a new law in the Kurdish region gave journalists "unprecedented freedoms."
Hong Kong, which is part of China, also dropped in rankings from free to partly free, a reflection of "the growing influence of Beijing over media and free expression in the territory."
Don't Miss
* Journalist jailed in Iran may seek pardon
* U.S. journalists to be tried in North Korea
* Journalists freed in Azerbaijan
* Read the report (PDF)
"Of particular concern were the appointment of 10 owners of Hong Kong media outlets to a mainland Chinese political advisory body, increased restrictions on film releases in the period surrounding the Olympics, and reports that critics of Beijing encountered growing difficulty in gaining access to Hong Kong media platforms."
The report cited deterioration of of freedoms in Taiwan, which has been characterized as East Asia's freest media environment. That's because of "legal pressures and attempts to control broadcast media outlets."
Italy dropped from free to partly free because of the "increased use of courts and libel laws to limit free speech, heightened physical and extralegal intimidation by both organized crime and far-right groups, and concerns over media ownership and influence," the report said.
It cited fears about media magnate Silvio Berlusconi becoming prime minister again. There are concerns about "the concentration of state-owned and private outlets under a single leader."
In the former Soviet Union, "legal pressure and attempts to control broadcast media outlets" were cited in Russia, Armenia and Kyrgyzstan. The report noted other problems in Russia, saying "reporters suffer from a high level of personal insecurity, and impunity for past murders or physical attacks against journalists is the norm."
Across Africa, there were "some improvements," citing developments in Comoros, Sierra Leone, Angola, and Liberia. But there were continued problems in places like Zimbabwe and Eritrea.
"Senegal took a significant step backward due to a dramatic increase in both legal and extralegal action against journalists and media houses, accompanied by overtly hostile rhetoric from the president and other officials," the report said.
The report cited strides in South Asian nations, ranking the once "not free" Maldives to "partly free." It mentioned a "new constitution protecting freedom of expression, the opening of additional private radio and television stations, the release of a prominent journalist from life imprisonment, and a general loosening of restrictions after the country's first democratic presidential election in October."
It said Bangladesh and Pakistan reversed declines in freedom of the media. But there were setbacks in Afghanistan and Sri Lanka, two countries racked by warfare.
In some countries in the Americas, such as Mexico, Bolivia and Ecuador, "attacks and official rhetoric against the media escalated." Venezuela and Cuba were ranked as not free, and there were "high levels of intimidation and self-censorship" in Colombia and Guatemala. Positive developments were noted in Guyana, Haiti and Uruguay.
The worst-rated countries in the world are Myanmar, Cuba, Eritrea, Libya, North Korea and Turkmenistan.
"Given the current economic climate, which is certain to place a further strain on media sustainability and diversity in rich and poor countries alike, pressures on media freedom are now looming from all angles and are increasingly threatening the considerable gains of the past quarter-century," the report said.
Saturday, April 11, 2009
Behind Microsoft’s ‘Apple tax’ gambit
Conficker wakes up, updates via P2P, drops payload
 The Conficker worm is finally doing something--updating via peer-to-peer between infected computers and dropping a mystery payload on infected computers, Trend Micro said on Wednesday.
Researchers were analyzing the code of the software that is being dropped onto infected computers but suspect that it is a keystroke logger or some other program designed to steal sensitive data off the machine, said David Perry, global director of security education at Trend Micro.
The software appeared to be a .sys component hiding behind a rootkit, which is software that is designed to hide the fact that a computer has been compromised, according to Trend Micro. The software is heavily encrypted, which makes code analysis difficult, the researchers said.
The worm also tries to connect to MySpace.com, MSN.com, eBay.com, CNN.com and AOL.com as a way to test that the computer has Internet connectivity, deletes all traces of itself in the host machine, and is set to shut down on May 3, according to the TrendLabs Malware Blog.
Because infected computers are receiving the new component in a staggered manner rather than all at once there should be no disruption to the Web sites the computers visit, said Paul Ferguson, advanced threats researcher for Trend Micro.
"After May 3, it shuts down and won't do any replication," Perry said. However, infected computers could still be remotely controlled to do something else, he added.
Last night Trend Micro researchers noticed a new file in the Windows Temp folder and a huge encrypted TCP response from a known Conficker P2P IP node hosted in Korea.
"As expected, the P2P communications of the Downad/Conficker botnet may have just been used to serve an update, and not via HTTP," the blog post says. "The Conficker/Downad P2P communications is now running in full swing!"
In addition to adding the new propagation functionality, Conficker communicates with servers that are associated with the Waledac family of malware and its Storm botnet, according to a separate blog post by Trend Micro security researcher Rik Ferguson.
The worm tries to access a known Waledac domain and download another encrypted file, the researchers said.
Conficker.C failed to make a splash a week ago despite the fact that it was programmed to activate on April 1. It has infected between 3 million and 12 million computers, according to Perry.
Initially, researchers thought they were seeing a new variant of the Conficker worm, but now they believe it is merely a new component of the worm.
The worm spreads via a hole in Windows that Microsoft patched in October, as well as through removable storage devices and network shares with weak passwords.
The worm disabled security software and blocks access to security Web sites. To check if your computer is infected you can use this Conficker Eye Chart or this site at the University of Bonn.
The Conficker worm is finally doing something--updating via peer-to-peer between infected computers and dropping a mystery payload on infected computers, Trend Micro said on Wednesday.
Researchers were analyzing the code of the software that is being dropped onto infected computers but suspect that it is a keystroke logger or some other program designed to steal sensitive data off the machine, said David Perry, global director of security education at Trend Micro.
The software appeared to be a .sys component hiding behind a rootkit, which is software that is designed to hide the fact that a computer has been compromised, according to Trend Micro. The software is heavily encrypted, which makes code analysis difficult, the researchers said.
The worm also tries to connect to MySpace.com, MSN.com, eBay.com, CNN.com and AOL.com as a way to test that the computer has Internet connectivity, deletes all traces of itself in the host machine, and is set to shut down on May 3, according to the TrendLabs Malware Blog.
Because infected computers are receiving the new component in a staggered manner rather than all at once there should be no disruption to the Web sites the computers visit, said Paul Ferguson, advanced threats researcher for Trend Micro.
"After May 3, it shuts down and won't do any replication," Perry said. However, infected computers could still be remotely controlled to do something else, he added.
Last night Trend Micro researchers noticed a new file in the Windows Temp folder and a huge encrypted TCP response from a known Conficker P2P IP node hosted in Korea.
"As expected, the P2P communications of the Downad/Conficker botnet may have just been used to serve an update, and not via HTTP," the blog post says. "The Conficker/Downad P2P communications is now running in full swing!"
In addition to adding the new propagation functionality, Conficker communicates with servers that are associated with the Waledac family of malware and its Storm botnet, according to a separate blog post by Trend Micro security researcher Rik Ferguson.
The worm tries to access a known Waledac domain and download another encrypted file, the researchers said.
Conficker.C failed to make a splash a week ago despite the fact that it was programmed to activate on April 1. It has infected between 3 million and 12 million computers, according to Perry.
Initially, researchers thought they were seeing a new variant of the Conficker worm, but now they believe it is merely a new component of the worm.
The worm spreads via a hole in Windows that Microsoft patched in October, as well as through removable storage devices and network shares with weak passwords.
The worm disabled security software and blocks access to security Web sites. To check if your computer is infected you can use this Conficker Eye Chart or this site at the University of Bonn.
Windows 7 beta upgrade won't be easy
 Those who want to move from the beta version of Windows 7 to the upcoming "release candidate" version will be able to do so, but it is going to take some work.
In a blog posting on Tuesday, Microsoft said that it is offering two options for going from the beta to the newer test version, which is due shortly. Neither is all that easy.
The recommended approach, Microsoft said, is to go back to Windows Vista and upgrade from that. Microsoft asked testers to follow this approach as it will help the company get more feedback on the experience that the typical user will have in going from Vista to Windows 7.
Those who really want to upgrade directly from the beta to the release candidate will be able to do so, but only using a series of convoluted steps.
"We know many people (including tens of thousands at Microsoft) are relying on the pre-release builds of Windows 7 for mission critical and daily work, making this step less than convenient," the company acknowledged in its blog. "We're working hard to provide the highest quality release we can and so we'd like to make sure for this final phase of testing we're supporting the most real world scenarios possible, which incremental build to build upgrades are not. At the same time everyone on the beta has been so great we wanted to make sure we at least offered an opportunity to make your own expert and informed choice about how to handle the upgrade."
The company also cautioned that the same hassles will apply for those moving from the release candidate to the final version of Windows 7.
Those who want to move from the beta version of Windows 7 to the upcoming "release candidate" version will be able to do so, but it is going to take some work.
In a blog posting on Tuesday, Microsoft said that it is offering two options for going from the beta to the newer test version, which is due shortly. Neither is all that easy.
The recommended approach, Microsoft said, is to go back to Windows Vista and upgrade from that. Microsoft asked testers to follow this approach as it will help the company get more feedback on the experience that the typical user will have in going from Vista to Windows 7.
Those who really want to upgrade directly from the beta to the release candidate will be able to do so, but only using a series of convoluted steps.
"We know many people (including tens of thousands at Microsoft) are relying on the pre-release builds of Windows 7 for mission critical and daily work, making this step less than convenient," the company acknowledged in its blog. "We're working hard to provide the highest quality release we can and so we'd like to make sure for this final phase of testing we're supporting the most real world scenarios possible, which incremental build to build upgrades are not. At the same time everyone on the beta has been so great we wanted to make sure we at least offered an opportunity to make your own expert and informed choice about how to handle the upgrade."
The company also cautioned that the same hassles will apply for those moving from the release candidate to the final version of Windows 7.
Yahoo & Microsoft Said to Be Weighing Ad Pact
Friday, April 10, 2009
Mobile Phone Tracking
Mobile Phone Location n U ?
Sky's The Limit: Time Warner's $150 Unlimited Bandwidth Plan
Security Firms Begin Poking New Conficker Variant
YouTube, Universal to launch 'Vevo' music video site
 Vivendi's Universal Music Group and Google Inc.'s YouTube have reached a deal to create a new premium music video service. The service, which is expected to launch in the coming months, is a bid to boost revenues from YouTube's phenomenal global usage. YouTube also gained an extension on the rights to feature content from Universal's catalog including U2 and 50 Cent, within YouTube videos.
The new service will be called Vevo, and it will offer higher quality music videos, as opposed to the typically lower quality content uploaded by users. The premium service, exclusive to Universal content, may also attract more big name advertisers who have been reluctant to advertise alongside user-generated content.
A boost in advertising rates will boost revenues for the content, which will be shared among Universal and YouTube.
Vivendi's Universal Music Group and Google Inc.'s YouTube have reached a deal to create a new premium music video service. The service, which is expected to launch in the coming months, is a bid to boost revenues from YouTube's phenomenal global usage. YouTube also gained an extension on the rights to feature content from Universal's catalog including U2 and 50 Cent, within YouTube videos.
The new service will be called Vevo, and it will offer higher quality music videos, as opposed to the typically lower quality content uploaded by users. The premium service, exclusive to Universal content, may also attract more big name advertisers who have been reluctant to advertise alongside user-generated content.
A boost in advertising rates will boost revenues for the content, which will be shared among Universal and YouTube.
YouTube, Universal to launch 'Vevo' music video site
Conficker worm finally stirs -- removal advice
 The (bad) April Fool's scare caused by the widely spread Conficker variety of malware has been followed by a spring to life by the Conficker worm, according to security firm Trend Micro. The firm has tracked Conficker updates to infected machines over the past few days, hinting that the authors are trying to cash in on their global botnet. Rather than instruct the worm to cause global chaos, it has started downloading fake anti-virus tools to nag users about phony infections and scam them into buying the "product".
It is estimated that as many as 12 million PCs worldwide are infected. The use of bogus software to extort money from uninformed users is nothing new at all, but it can be very profitable to the individuals behind the scam and a total nightmare for anyone who falls into the trap and pays for a clean-up that never happens. The spread of Conficker emphasizes just how many Windows machines are running without Automatic Updates enabled or adequate security software.
DETECTION & REMOVAL
To figure out whether you are infected with the Conficker worm is to try the usual tricks. Firstly, check the websites of common security tools like Symantec, AVG and Avira. If none of those would load, you may be infected, as Conficker blocks access to the sites. Another good test is to check the status of several services (Start -> Run -> services.msc). If Automatic Updates, Background Intelligent Transfer Service, Error Reporting Service or Windows Defender (or other security services you did not disable yourself) have been disabled without your knowledge, or cannot be started, this could be another sign of infection.
If you have any concerns after these checks, then downloading and running a removal tool might be a good idea.
Removal Tools
McAfee AVERT W32/Conficker Stinger - Download!
Symantec W32.Downadup Removal Tool 1 - Download! (CNET)
Sophos Conficker Cleanup Tool (Stand-Alone Computer) - Download!
Sophos Conficker Cleanup Tool (Network Removal) - Download!
Eset Win32/Conficker Worm Removal Tool - Download! (CNET)
Anti-Virus
Avira AntiVir Personal - Download!
AVG Free Edition - Download!
Microsoft Patch
MS08-067 - addresses a vulnerability in Microsoft Windows (KB 958644) - Download!
The (bad) April Fool's scare caused by the widely spread Conficker variety of malware has been followed by a spring to life by the Conficker worm, according to security firm Trend Micro. The firm has tracked Conficker updates to infected machines over the past few days, hinting that the authors are trying to cash in on their global botnet. Rather than instruct the worm to cause global chaos, it has started downloading fake anti-virus tools to nag users about phony infections and scam them into buying the "product".
It is estimated that as many as 12 million PCs worldwide are infected. The use of bogus software to extort money from uninformed users is nothing new at all, but it can be very profitable to the individuals behind the scam and a total nightmare for anyone who falls into the trap and pays for a clean-up that never happens. The spread of Conficker emphasizes just how many Windows machines are running without Automatic Updates enabled or adequate security software.
DETECTION & REMOVAL
To figure out whether you are infected with the Conficker worm is to try the usual tricks. Firstly, check the websites of common security tools like Symantec, AVG and Avira. If none of those would load, you may be infected, as Conficker blocks access to the sites. Another good test is to check the status of several services (Start -> Run -> services.msc). If Automatic Updates, Background Intelligent Transfer Service, Error Reporting Service or Windows Defender (or other security services you did not disable yourself) have been disabled without your knowledge, or cannot be started, this could be another sign of infection.
If you have any concerns after these checks, then downloading and running a removal tool might be a good idea.
Removal Tools
McAfee AVERT W32/Conficker Stinger - Download!
Symantec W32.Downadup Removal Tool 1 - Download! (CNET)
Sophos Conficker Cleanup Tool (Stand-Alone Computer) - Download!
Sophos Conficker Cleanup Tool (Network Removal) - Download!
Eset Win32/Conficker Worm Removal Tool - Download! (CNET)
Anti-Virus
Avira AntiVir Personal - Download!
AVG Free Edition - Download!
Microsoft Patch
MS08-067 - addresses a vulnerability in Microsoft Windows (KB 958644) - Download!
Tornado roars through Arkansas town, kills 3
Monday, March 16, 2009
Tips Bypass Internet Akses : 2 - Freegate
Sunday, March 15, 2009
Bypass Firewall Part I dengan Aplikasi proxy gratisan
 Satu lagi neh aplikasi free proxy tandingan dari tutorial yang pernah di posting oleh mahadewa. Aplikasi ini berasal dari negeri Jerman kayaknya. Soalnya banyak IP german yang disediakan. Situs resminya adalah www.your-freedom.net. Tapi disini aku tidak membahas apa itu proxy, cari aja di google kalau mau mengetahui pengertian lengkap dari proxy. Tapi kegunaan utama proxy adalah untuk melewati firewall yang dibuat untuk membatasi koneksi internet kita.
Apa itu firewall? nah terpaksa cari lagi deh di google :D. Hmm tapi aku cerita sedikit tentang firewall menurut versi aku.
Gini deh, klo kita sedang surfing or lagi depan komputer yang terhubung ke internet entah itu kita memakai laptop dirumah, di cafe, atau dimana aja, bisa juga kita lagi disebuah warnet. Ketika kita ingin membuka sebuah situs yang didalamnya ada konten pornograpi, secara (bahasa gaul dikit) pemerintah kita lagi giat2nya menghimbau kepada semua ISP (Internet Service Provider/penyedia jasa internet) untuk memblokir semua situs yang memuat konten SARA,Pornographi dan sebagainya yang tercantum dalam UUITE yang dikeluarkan beberapa waktu lalu. Nah, ketika kita membuka situs tersebut, yang ada hanyalah tampilan browser kosong yang berisi peringatan bahwa site tersebut telah di block oleh sang admin yang menyediakan koneksi internet kita.
Kasus satu lagi yang sering terjadi adalah kita tidak bisa mengakses sebuah situs karena IP kita telah di block oleh empunya situs. Jadi Fungsi utama dari kita memakai proxy adalah untuk melewati sebuah firewall dan juga memanipulasi pembacaan IP dari sebuah situs yang ingin kita kunjungi. Masih banyak kasus kasus lain yang memaksa kita untuk memakai sebuah proxy yang tidak bisa aku jelasin disini, karena inti dari tulisan ini adalah cara memakai aplikasi proxy gratisan dari www.your-freedom.net.
Tutorial ini sebenarnya dibuat bukan untuk mengajari seseorang untuk berbuat nakal :D, tapi lebih untuk sebuah pembelajaran dalam mengenal fungsi umum dari sebuah kata proxy.
Sebelum menggunakan aplikasi ini, kita diwajibkan untuk register disitus utamanya www.your-freedom.net atau bisa langsung daftar dengan meng-klik First visit? Click here to register dibawah kolom login. Tetapi sebelum kita masuk lebih dalam pada proses registrasi ada baiknya kita mendownload aplikasi yang akan kita gunakan nantinya. Klik download dan pilih full windows installer klo mau yang paling lengkap. Filenya berukuran sekitar 11 Mb.
Setelah mengisi beberapa field yang diawajibkan diisi seperti buat email baru, selanjutnya yaitu proses verifikasi dengan cara membuka email yang kita masukkan pada saat registrasi.
Kita akan mendapatkan sebuah acount YF (your-freedom) baru setelah proses verifikasi, yang akan kita gunakan untuk login melalui situsnya atau login melalui aplikasi YF.
Untuk acount YF gratisan (free) kita mendapatkan beberapa fasilitas diantaranya adalah koneksi max 64kbps selama 6 jam, tapi setiap 1 jam koneksi akan terputus, peringatan pemutusan koneksi diberikan 5 menit sebelum terjadi pemutusan. Reconect ulang dengan memasukkan kode angka yang diberikan. Weks napa dah loncat kesana :D
Now, aku anggap proses download, registrasi, instalasi aplikasi di windows sudah selesai. Sekarang tata cara penggunaannya...cari minum dulu :) bersambung ke part II
Satu lagi neh aplikasi free proxy tandingan dari tutorial yang pernah di posting oleh mahadewa. Aplikasi ini berasal dari negeri Jerman kayaknya. Soalnya banyak IP german yang disediakan. Situs resminya adalah www.your-freedom.net. Tapi disini aku tidak membahas apa itu proxy, cari aja di google kalau mau mengetahui pengertian lengkap dari proxy. Tapi kegunaan utama proxy adalah untuk melewati firewall yang dibuat untuk membatasi koneksi internet kita.
Apa itu firewall? nah terpaksa cari lagi deh di google :D. Hmm tapi aku cerita sedikit tentang firewall menurut versi aku.
Gini deh, klo kita sedang surfing or lagi depan komputer yang terhubung ke internet entah itu kita memakai laptop dirumah, di cafe, atau dimana aja, bisa juga kita lagi disebuah warnet. Ketika kita ingin membuka sebuah situs yang didalamnya ada konten pornograpi, secara (bahasa gaul dikit) pemerintah kita lagi giat2nya menghimbau kepada semua ISP (Internet Service Provider/penyedia jasa internet) untuk memblokir semua situs yang memuat konten SARA,Pornographi dan sebagainya yang tercantum dalam UUITE yang dikeluarkan beberapa waktu lalu. Nah, ketika kita membuka situs tersebut, yang ada hanyalah tampilan browser kosong yang berisi peringatan bahwa site tersebut telah di block oleh sang admin yang menyediakan koneksi internet kita.
Kasus satu lagi yang sering terjadi adalah kita tidak bisa mengakses sebuah situs karena IP kita telah di block oleh empunya situs. Jadi Fungsi utama dari kita memakai proxy adalah untuk melewati sebuah firewall dan juga memanipulasi pembacaan IP dari sebuah situs yang ingin kita kunjungi. Masih banyak kasus kasus lain yang memaksa kita untuk memakai sebuah proxy yang tidak bisa aku jelasin disini, karena inti dari tulisan ini adalah cara memakai aplikasi proxy gratisan dari www.your-freedom.net.
Tutorial ini sebenarnya dibuat bukan untuk mengajari seseorang untuk berbuat nakal :D, tapi lebih untuk sebuah pembelajaran dalam mengenal fungsi umum dari sebuah kata proxy.
Sebelum menggunakan aplikasi ini, kita diwajibkan untuk register disitus utamanya www.your-freedom.net atau bisa langsung daftar dengan meng-klik First visit? Click here to register dibawah kolom login. Tetapi sebelum kita masuk lebih dalam pada proses registrasi ada baiknya kita mendownload aplikasi yang akan kita gunakan nantinya. Klik download dan pilih full windows installer klo mau yang paling lengkap. Filenya berukuran sekitar 11 Mb.
Setelah mengisi beberapa field yang diawajibkan diisi seperti buat email baru, selanjutnya yaitu proses verifikasi dengan cara membuka email yang kita masukkan pada saat registrasi.
Kita akan mendapatkan sebuah acount YF (your-freedom) baru setelah proses verifikasi, yang akan kita gunakan untuk login melalui situsnya atau login melalui aplikasi YF.
Untuk acount YF gratisan (free) kita mendapatkan beberapa fasilitas diantaranya adalah koneksi max 64kbps selama 6 jam, tapi setiap 1 jam koneksi akan terputus, peringatan pemutusan koneksi diberikan 5 menit sebelum terjadi pemutusan. Reconect ulang dengan memasukkan kode angka yang diberikan. Weks napa dah loncat kesana :D
Now, aku anggap proses download, registrasi, instalasi aplikasi di windows sudah selesai. Sekarang tata cara penggunaannya...cari minum dulu :) bersambung ke part II
Hackers Work's
How Cell-phone Viruses Work on The Phone
Spot the Tiny Phishing Trick
Friday, March 13, 2009
Melewati Akses Internet Yang Diblokir
- Web proxy Dengan menggunakan web proxy kita bisa dengan mudah mengakses suatu halaman di internet yg tidak bisa kita akses secara langsung (direct connection) atau pun melalui proxy pada jaringan internet yg kita pakai. Web proxy dapat kita cari dengan mudah melalui Google, salah satunya www.hidemyass.com. Untuk mengakses halaman yg ingin dituju, masukkan URL halaman tsb pada box kemudian tekan tombol HideMyAss.
- Online translator Pada dasarnya online translator ditujukan untuk menerjemahkan bahasa dari sebuah halaman website namun online translator ini bisa jg dijadikan sebagai web proxy. Salah satu dari online translator itu adalah Google Translate.
- Ultrasurf, Freegate dan GPass Ketiga software ini diciptakan oleh para pembuatnya bagi org2 yg tinggal di negara Cina. Tujuan dari software ini adalah utk membypass firewall yg dibuat oleh pemerintah Cina sehingga org2 yg tinggal di negara Cina bisa dengan mudah mengakses informasi yg berasal dari luar negara Cina. Dengan menggunakan salah satu dari ketiga software ini, kita jg bisa membypass firewall jaringan internet untuk mengakses halaman internet yg diblokir. Ketiga software ini dapat berjalan di Windows tanpa perlu instalasi sehingga bersifat portabel dan jg ukurannya sangat kecil, sekitar 200 KB. Penggunaan ketiga sofware ini dapat anda lihat disini : Ultrasurf, Freegate, GPass
- Your Freedom Oleh para pengembangnya, Your Freedom diciptakan untuk membypass koneksi internet yg dibatasi oleh firewall dan filtering proxy. Your Freedom mempunyai sekitar 24 proxy server yg tersebar di benua Amerika, Eropa dan Asia. Software ini dapat dijalankan pada Windows dengan menggunakan platform Java. Ada 4 paket yg ditawarkan untuk dapat menggunakan Your Freedom, yaitu paket Free, Basic, Enhanced dan Total. Artikel selengkapnya beserta penggunaannya dapat dilihat disini.
- ...
Buka proteksi internet kantor
 , namun disini saya mau membahas salah satu cara yang menurut saya efektif (menurut saya lho ini) yaitu menggunakan toonel alias tunel atau software proxy (benar ga sih istilahnya begitu?)
Sebenernya kalo mau buka web yang di blok sama admin ngga harus pake toonel atau software2 proxy tapi bisa juga pake anonymous web, anonymous web ini sama juga menggunakan fasilitas proxy melalui web. nah dibawah ini adalah salah satu (salah banyak ding) web yang bisa digunakan untu melewati proteksi web oleh admin network kampus, kantor atau instansi tempat anda berinternet
, namun disini saya mau membahas salah satu cara yang menurut saya efektif (menurut saya lho ini) yaitu menggunakan toonel alias tunel atau software proxy (benar ga sih istilahnya begitu?)
Sebenernya kalo mau buka web yang di blok sama admin ngga harus pake toonel atau software2 proxy tapi bisa juga pake anonymous web, anonymous web ini sama juga menggunakan fasilitas proxy melalui web. nah dibawah ini adalah salah satu (salah banyak ding) web yang bisa digunakan untu melewati proteksi web oleh admin network kampus, kantor atau instansi tempat anda berinternet - http://anonymouse.org/
- http://notyourip.com/
- http://ninjaproxy.com/
- http://www.unblockglobal.com/
- http://www.dontyouknow.info/
- http://www.yourpcsucks.com/
- http://www.unblock7.com/
- http://hidemyass.com/
- http://youhide.com/
- Download Toonel freegate (toonel yang bagus menurut saya) bisa anda download di sini Download freegate ver 677 http://www.ziddu.com/download/2692210/fg677p.exe.html
- Setelah selesai download langsung saja jalankan freegate (tinggal dobel klik)
- Nah kalo freegate bekerja dengan lancar tanpa gangguan, freegate akan mencari proxy yang aktif dan mengkonekkan alias menghubungkan anda denga proxy tersebut, dan secara otomatis juga setelah freegate connect dia akan membuka Internet Explorer secara sendirinya (datang tak dijemput pulang tak diantar) kaya jelangkung... hiiii
- Nah internet exsplorer siap digunakan untuk bersurfing dan ber browsing ke situs yang diblokir. selesai deh...
- tinggal masukin aja alamat yang diblokir lewat Internet Eksplorer.. Selesai kan??
 hampir lupa..
nah ini tips n trik tambahan buat para pencinta Moziilla Firefox seperti saya..
hampir lupa..
nah ini tips n trik tambahan buat para pencinta Moziilla Firefox seperti saya..  supaya setingan dari freegate bisa teraplikasi atau bisa digunakan dalam firefox kita tinggal set aja proxy dari firefox.. caranya :
supaya setingan dari freegate bisa teraplikasi atau bisa digunakan dalam firefox kita tinggal set aja proxy dari firefox.. caranya : - buka tool - Option - buka tab advanced - buka tab Network - Setting - pilih manual proxy configuration
- isi kolom HTTP Proxy dengan ip : 127.0.0.1 dan isi port : 8580 setelah itu centang "use this proxy for all protocol"
- nah jadi deh... kalo ngga mau repot2 gonta ganti n ngga mau cape ngetik ip proxy tadi anda bisa gunakan add-ons dari firefox yang bernama switch proxy bisa di download di alamt ini : https://addons.mozilla.org/extension...cation=firefox dengan add-ons itu anda dapat menyimpan settingan proxy dan dapat menggantinya sewaktu2
- toonel freegate ini juga bisa memperlancar surfing dan browsing, entah ini perasaan saya saja atau memang seperti itu adanya, karena selama saya menggunakan freegate kayanya kecepatan internetnya jadi bertambah, saya yang biasanya (baru seminggu ding jadi belum bisa dikatakan biasa
 ) menggunakan indosat m2 broom paket unlimited yang rata-rata kecepatannya 8 kBps pernah juga sampai 30 kBps cuman sedetik tapi (maklum di desa saya belum ada 3g) bisa naik sampai 15 kBps ke atas bahkan sampai 21 - 40 kBps.. ngga tau juga apa cuman perasaan saya atau memang tambah banter...
mending dicoba aja deh...
) menggunakan indosat m2 broom paket unlimited yang rata-rata kecepatannya 8 kBps pernah juga sampai 30 kBps cuman sedetik tapi (maklum di desa saya belum ada 3g) bisa naik sampai 15 kBps ke atas bahkan sampai 21 - 40 kBps.. ngga tau juga apa cuman perasaan saya atau memang tambah banter...
mending dicoba aja deh...
Nama E-mail Pengaruhi Jumlah Spam
Terjangan spam alias pesan sampah ternyata tidak sembarang menyerbu alamat e-mail. Dalam studi University of Cambridge di Inggris diungkap bahwa jumlah spam yang diterima pemakai e-mail tergantung pada huruf pertama nama e-mailnya. Dengan menganalisis sekitar 500 juta spam yang beredar di Inggris, ditemukan bahwa alamat e-mail yang dimulai dengan huruf yang umum dipakai kemungkinan kuantitas spam-nya mencapai 40 persen. Sedangkan alamat yang dimulai dengan huruf yang tidak umum, maka kuantitas spam hanya mencapai seperlima di inbox mereka.
Menurut studi ini, jika huruf pertama dalam alamat e-mail dimulai dengan J, A, U, I, R, P, M, atau S, maka jumlah spam yang diterima bisa sampai dua kali lipat dibanding dengan alamat e-mail yang dimulai dengan huruf Q, Z, W, Y atau F.
Sayangnya, studi ini tak menyimpulkan penyebab pasti fenomena itu. Dr Richard Clayton, akademisi Cambridge University yang membesut studi ini hanya mengemukakan bahwa mungkin, hal itu disebabkan lebih banyak nama e-mail dimulai dengan huruf di barisan pertama daripada yang kedua sehingga kuantitas spam-nya lebih banyak.
Temuan tersebut diharapkan bisa membantu dibuatnya teknik tertentu dalam menangkal spam.
DETIKINET
Saturday, February 28, 2009
Facebook Indonesia
Facebook, formerly Thefacebook, is a free-access social networking website that is operated and privately owned by Facebook, Inc. Users can join networks organized by city, workplace, school, and region to connect and interact with other people. People can also add friends and send them messages, and update their personal profiles to notify friends about themselves. The website’s name refers to the paper facebooks depicting members of a campus community that some US colleges and preparatory schools give to incoming students, faculty, and staff as a way to get to know other people on campus.
Compared to Friendster? Facebook is far more “adult”. Views FS is very fancy and very suitable for young people. FB is much more elegant because the view can not customize the indiscriminate, so very fitting for a serious adult. More the top person (adults) joined, such as Amien Rais, Andi Noya, Faisal Basri, etc. From politicians, artists, lecturers, scientists, etc. The more sharing thoughts directly from Facebook, very effective. Compared to FS, FB is still far in Indonesia, even though globally the largest is MySpace then facebook. Both users have more than other competitors such as Friendster and Orkut (Google’s).
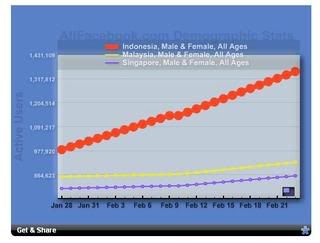
Below the number of users online social networking in Asian (in million / million users, 1 person can have more than 1 user).
Friendster (65 million users) Facebook (14 million) MySpace (15 million) CyWorld (Korea, 14 million) Hi5 (10 million) Orkut (10 million) Xiaonei (China, 5 million) 51.com (China, 5 million) Bebo (4 million). Source: Inside Facebook
Some other data of Facebook statistical : - More than 150 million users worldwide - Over half the users are outside the school / college - More than 700 million photo uploads per month - More than 4 million video uploads per month - 2.6 billion minutes spent on Facebook per day - Users age 25 years is the most rapid growth
Mark Zuckerberg founded Facebook while he was a student at Harvard University. Website membership was initially limited to Harvard students, but was expanded to other colleges in the Boston area, the Ivy League, and Stanford University. It later expanded further to include any university student, then high school students, and, finally, to anyone aged 13 and over. The website currently has more than 175 million active users worldwide.
Facebook has met with some controversy over the past few years. It has been blocked intermittently in several countries including Syria and Iran. It has also been banned at many places of work to discourage employees from wasting time using the service. Privacy has also been an issue, and it has been compromised several times. It is also facing several lawsuits from a number of Zuckerberg’s former classmates, who claim that Facebook had stolen their source code and other intellectual property.
2008 may be spelled Facebook is a year in Indonesia. Imagine, 2008 year ago the growth of Facebook reached 645% or more than 6-fold from the previous year. At this time there were 831 thousand Facebook users are from Brazil (0.4% of our population 237 million). One review said that the features of Facebook in Australia would trigger the growth of this high.
However, consider “culture” of Indonesia social networking which is very high on the Internet, with so Populer Friendster in Indonesia, then it is not strange that this service can be very popular in Indonesia.
Below Facebook Demographic Statistics for Indonesia
Source 2009 : http://allfacebook.com/facebook-demographic-statistics/ http://en.wikipedia.org/wiki/Facebook http://teknohikmah.blogspot.com/2009/01/facebook-terobos-dunia-internet.html
Kiamat 2012 (Day of Resurrection 2012)
On the internet at this time many words that the Maya tribe predicted who lived in southern Mexico or Guatemala on the Day of Resurrection will occur on 21 December 2012.
In the manuscript of the tribe known heritage astronomical and calendar system mentioned on this date will appear the waves so large galaxy that resulted in interruption of all activities in the face of this Earth. Outside the prediction Maya tribe that has not known the basic calculations, according to Deputi Bidang Sains Pengkajian dan Informasi Kedirgantaraan, Lembaga Penerbangan dan Antariksa Nasional (Lapan), Bambang S Tedjasukmana, estimated phenomena that can appear around the year 2011-2012 is sun storms. Prediction is based on the monitoring center monitors the weather in outer space some countries since the 1960s, and by Lapan in Indonesia since 1975.
Described, Sri Kaloka, Head of The Center for Science Space Lapan, storms occur when Sun appears Flare and Coronal Mass Ejection (CME). Flare is a big explosion in the atmosphere of the Sun charged equivalent to 66 million Hiroshima atomic bomb explosion. The CME is a very big explosion that caused hurl particles speed 400 kilometers per second.
Sun weather disturbances can affect the condition of cargo to the outer magnet Earth, further impact on the electricity system, transportation, relying on the satellite navigation global positioning system (GPS) and communication systems that use satellite communications and high frequency waves (HF), and may be dangerous to life or human health. “Because the Earth magnet interference, ” said Sri. Step antisipatif
From the Sun, billions of particles to the electron layer ionosfer Earth in four days time, said Jiyo Harjosuwito, Head of Group Research Ionosfer and Propagasi Radio Waves. The impact of the electron charge particles in the Earth polar magnet held for several days. During that time antisipatif step can be done to reduce the impact caused.
Anticipate the emergence of the outer waves, continue Bambang, Lapan has building the central system to monitor the weather in outer space integrated Science Center Utilization Space Lapan Bandung. Object monitored, among other layers ionosfer and geomagnetik, and radio waves. This system will be fully operational in January 2009 to come.
Antisipatif steps which have been made Lapan such as contact the parties that may be affected by the storm’s outer emergence, Dephankam namely, military, Dephub, PLN, and Depkominfo and local governments. Currently training for local government officials who operate the HF radio has been made since long ago, now there are about 500 people trained in the radio signal interference.
Bambang expects PLN to take steps antisipatif with the extinction of the electricity system that does not happen that impact worse. Therefore, socialization should be done in the community when it steps will be taken.
In addition, flights and cruises that rely on GPS satellite navigation system as the system should use the manual when the storm occurred outer space, living in the guide base or landing aircraft.
Electron density changes due to weather outer, said Lapan researcher from the PPSA, Effendi, can change the speed of radio waves when passing through ionosfer so giving rise delay propagasi on the GPS signal.
These changes lead to distortions in the determination of the distance and position. In addition, components microelectronic on satellite navigation and communications will be damaged, so that the acceleration of the life, so that it can not work anymore.
Currently, Lapan have developed modeling for planning the use of the frequency interference to HF radio communications. “Now we have prepared the same field modeling for navigation,” said Bambang.
source : http://www.kompas.com/read/xml/2008/11/26/13072198/isu.kiamat.tahun.2012.yang.meresahkan
Google Ocean Temukan Petunjuk Baru Kota Atlantis
 TEKNOLOGI Google Ocean yang merupakan bagian dari Google Earth temukan petunjuk baru bagi misteri kota bawah laut Atlantis. Sebuah pola menyerupai pola sebuah kota berhasil ditemukan di dasar laut dekat kepulauan Canary, Samudera Atlantik, dan menjadi petunjuk terbaru bagi misteri Atlantis.
Para peneliti yang kerap memburu misteri kota bawah laut Atlantis, tampaknya dapat sedikit tersenyum lega sekarang. Hal ini dikarenakan kegiatan penelitian mereka kini menjadi lebih mudah dengan memanfaatkan Google Ocean.
Hingga hari ini belum ada satu pun penelitian yang berhasil membuktikan keberadaan kota raksasa bawah air tersebut. Namun, misteri keberadaan Atlantis tetap membuat para peneliti berusaha ‘mengupdate’ informasi terbaru seputar keberadaan Atlantis.
Kini, Google Ocean, berhasil menangkap gambaran dari satelit pemancar Google Earth berupa guratan-guratan tekstur di dasar laut. Guratan-guratan yang menjadi dasar perkiraan kota Atlantis tersebut merupakan guratan-guratan yang berada pada jarak 620 mil dari bagian pantai Barat Laut Afrika dekat dengan kepulauan Canary pada bagian dasar Samudera Atlantik.
Google Ocean merupakan temuan para ilmuan Mountain View (kota markas Google) yang kini mencoba mengeplorasi ke dalam laut. Bukan hanya laut, tetapi juga dasar lautnya. Format Peta dari Google Ocean ini, memungkinkan penggunanya untuk melihat-lihat isi lautan dengan tombol navigasi.
Tidak hanya itu, Google Ocean juga memiliki data-data penting seputar dasar laut, seperti; kondisi cuaca di sekitar laut tersebut, jenis koral yang hidup di dasar lautan itu, bangkai kapal terkenal yang ada di dasar lautan itu, dan tak ketinggalan arus lautan itu.
Berdasarkan gambar yang berhasil ditangkap satelit Google Ocean, tampak bentuk persegi panjang yang kira-kira berukuran sama dengan kota Wales, Inggris dan gambar tersebut diperkirakan sebuah fosil kota bawah laut. Hal ini juga tergambar pada alat eksplorasi seorang ahli aeronautical yang juga mengklaim bahwa gambar tersebut juga gambar sebuah kota. Guratan tersebut dapat kita temukan pada koordinat 31 15’15.53N 15’30.53W.
Pernyataan tersebut didukung oleh beberapa peneliti Atlantis karena koordinat tersebut sesuai dengan deskripsi yang dilakukan oleh Filsafat, Yunani, Plato. Menurut Plato kota tesebut tenggelam setelah para penduduknya gagal untuk menguasai Athena sekitar tahun 9000 SM.
Dr Charles Orser dari Universitas New York menyatakan bahwa penemuan yang memanfaatkan teknologi Google Earth ini sangat mengagumkan dan sebaiknya dilakukan penelitian lebih lanjut.
Bernie Bamford (38) dari Chester yang menemukan pola tersebut, kemudian membandingkannya dengan skema milik Milton Keynes, sebuah desain tata kota dari Buckinghamshire. Setelah membandingkan pola tersebut, Bernie mengatakan kalau pola itu merupakan buatan manusia.
Sejarah Atlantis sendiri telah menarik jutaan imajinasi manusia selama berabad-abad. Dan sebelum penemuan ini, ada yang memperkirakan kalau kota tersebut berada pada lepas pantai Siprus dan ada pula di bagian selatan Spanyol.
Menurut Plato, Atlantis merupakan sebuah pulau yang lebih besar dari Libya dan Asia yang dijadikan satu serta berada di depan Pilar Hercules – Selat Gibraltar. Atlantis merupakan negeri dengan kekayaan yang luar biasa, peradaban yang maju, serta keindahan yang lenyap oleh gempa bumi dan banjir 9000 tahun kemudian karena ketidak mampuan mereka untuk mengatasi global warming. (*/OL-02)
TEKNOLOGI Google Ocean yang merupakan bagian dari Google Earth temukan petunjuk baru bagi misteri kota bawah laut Atlantis. Sebuah pola menyerupai pola sebuah kota berhasil ditemukan di dasar laut dekat kepulauan Canary, Samudera Atlantik, dan menjadi petunjuk terbaru bagi misteri Atlantis.
Para peneliti yang kerap memburu misteri kota bawah laut Atlantis, tampaknya dapat sedikit tersenyum lega sekarang. Hal ini dikarenakan kegiatan penelitian mereka kini menjadi lebih mudah dengan memanfaatkan Google Ocean.
Hingga hari ini belum ada satu pun penelitian yang berhasil membuktikan keberadaan kota raksasa bawah air tersebut. Namun, misteri keberadaan Atlantis tetap membuat para peneliti berusaha ‘mengupdate’ informasi terbaru seputar keberadaan Atlantis.
Kini, Google Ocean, berhasil menangkap gambaran dari satelit pemancar Google Earth berupa guratan-guratan tekstur di dasar laut. Guratan-guratan yang menjadi dasar perkiraan kota Atlantis tersebut merupakan guratan-guratan yang berada pada jarak 620 mil dari bagian pantai Barat Laut Afrika dekat dengan kepulauan Canary pada bagian dasar Samudera Atlantik.
Google Ocean merupakan temuan para ilmuan Mountain View (kota markas Google) yang kini mencoba mengeplorasi ke dalam laut. Bukan hanya laut, tetapi juga dasar lautnya. Format Peta dari Google Ocean ini, memungkinkan penggunanya untuk melihat-lihat isi lautan dengan tombol navigasi.
Tidak hanya itu, Google Ocean juga memiliki data-data penting seputar dasar laut, seperti; kondisi cuaca di sekitar laut tersebut, jenis koral yang hidup di dasar lautan itu, bangkai kapal terkenal yang ada di dasar lautan itu, dan tak ketinggalan arus lautan itu.
Berdasarkan gambar yang berhasil ditangkap satelit Google Ocean, tampak bentuk persegi panjang yang kira-kira berukuran sama dengan kota Wales, Inggris dan gambar tersebut diperkirakan sebuah fosil kota bawah laut. Hal ini juga tergambar pada alat eksplorasi seorang ahli aeronautical yang juga mengklaim bahwa gambar tersebut juga gambar sebuah kota. Guratan tersebut dapat kita temukan pada koordinat 31 15’15.53N 15’30.53W.
Pernyataan tersebut didukung oleh beberapa peneliti Atlantis karena koordinat tersebut sesuai dengan deskripsi yang dilakukan oleh Filsafat, Yunani, Plato. Menurut Plato kota tesebut tenggelam setelah para penduduknya gagal untuk menguasai Athena sekitar tahun 9000 SM.
Dr Charles Orser dari Universitas New York menyatakan bahwa penemuan yang memanfaatkan teknologi Google Earth ini sangat mengagumkan dan sebaiknya dilakukan penelitian lebih lanjut.
Bernie Bamford (38) dari Chester yang menemukan pola tersebut, kemudian membandingkannya dengan skema milik Milton Keynes, sebuah desain tata kota dari Buckinghamshire. Setelah membandingkan pola tersebut, Bernie mengatakan kalau pola itu merupakan buatan manusia.
Sejarah Atlantis sendiri telah menarik jutaan imajinasi manusia selama berabad-abad. Dan sebelum penemuan ini, ada yang memperkirakan kalau kota tersebut berada pada lepas pantai Siprus dan ada pula di bagian selatan Spanyol.
Menurut Plato, Atlantis merupakan sebuah pulau yang lebih besar dari Libya dan Asia yang dijadikan satu serta berada di depan Pilar Hercules – Selat Gibraltar. Atlantis merupakan negeri dengan kekayaan yang luar biasa, peradaban yang maju, serta keindahan yang lenyap oleh gempa bumi dan banjir 9000 tahun kemudian karena ketidak mampuan mereka untuk mengatasi global warming. (*/OL-02)
Hearst Planning Electronic Reader Alternative To Kindle
Hearst, which has seen its own revenue plummet as advertisers shift an increasing amount of their spending to the Web, is planning to launch an e-reader with a large-format screen this year, Fortune magazine reported Friday. The device would be big enough for the layout and advertising requirements of newspapers and magazines.
Hearst Corp.'s plans to launch a wireless electronic reader for viewing the publisher's newspapers and magazines reflects the kind of experimentation deemed pivotal to finding a business model that can compete in an era of the content-free Internet. Hearst, which has seen its own revenue plummet as advertisers shift an increasing amount of their spending to the Web, is planning to launch an e-reader with a large-format screen this year, Fortune magazine reported Friday. The device would be big enough for the layout and advertising requirements of newspapers and magazines.
scan Virus HP Dengan Kaspersky
Ngomong-ngomong mengenai virus ponsel, sebenarnya apa sih virus ponsel itu? Virus pada ponsel berarti segala program atau kode yang dapat menyebabkan aplikasi atau fitur ponsel tidak dapat digunakan semestinya. Biasanya virus disamarkan dalam bentuk yang menarik seperti game ataupun gambar. Supaya lebih menarik lagi, permainan ataupun gambar tersebut diselipkan kata-kata seronok.
Virus yang dapat menyerang ponsel dan PDA pertama kali ditemukan sekitar Juli 2004, saat ahli selular menemukansoftware yang mampu berpindah dan memperbanyak diri dengan perantara Bluetooth. Virus ini dinamakan Cabir. Setelah itu mulai bermunculan virus lain, seperti Commwarrior-A yang menyusup pada game The Mosquitos. Lalu muncul lagi virus ponsel yang dapat mengirim MMS otomatis ke nomor yang ada dalam inbox. Virus bukan satu-satunya perusak ponsel.
Ada worm atau cacing yang bertempat tinggal pada memori ponsel yang aktif dan bisa menduplikasi dengan sendirinya. Worm menyebar ke ponsel lain melalui e-mail, chatting, LAN, dan Bluetooth.
Berbagai Virus PonselContoh virus jenis worm ini adalah Cabir. Cabir menyebar melalui koneksi Bluetooth dan masuk ke dalam ponsel melalui inbox, misalnya berupa file dengan ekstensi sys (mirip aplikasi Symbian). Saat file sis tersebut diklik dan di-install, Cabir mulai mencari mangsa baru, yaitu ponsel dengan akses Bluetooth terbuka untuk menginfeksinya. Nama lain dari Cabir adalah SymbOS/Cabir.A, atau bisa juga dinamai Cabir.A,Worm atau bisa juga disebut virus Caribe.
Cabir akan mengaktifkan Bluetooth secara periodik sekitar 15-20 menit sekali. Tidak ada kerusakan file yang terjadi apabila ponsel kita terkena virus ini, tapi baterai akan cepat habis karena dipakai untuk mencari perangkat Bluetoothaktif lainnya. Untuk mencegahnya, yang dapat dilakukan adalah mematikan fitur Bluetooth di ponsel kita dan kita hanya mengaktifkan saat dibutuhkan saja.
Selain Cabir, salah satu jenis virus worm lainnya adalah Commwarrior yang menyebar melalui MMS dan koneksiBluetooth. Setiap tanggal 14, ponsel akan me-reset dengan sendirinya. Nama lain dari Commwarrior antara lain adalah SymbOS/commwarrior.a.
Commwarrior menyebar dengan cara mengirim file yang menarik ke ponsel kita. Salah satu cara untuk mencegahnya adalah dengan tidak menggunakan Bluetooth secara sembarangan dan jangan menerima file yang tidak diketahui asal-usulnya. Perusak ponsel lainnya adalah Trojan Horse. Trojan Horse adalah suatu program jahat yang berpura-pura ramah. Trojan dapat merusak program pada ponsel. Trojan tidak dapat menduplikasi dirinya seperti worm.
Salah satu jenis dari Trojan adalah Skulls dengan nama lengkap SymbOS.skulls. Nama lain dari virus ini adalah SKULLS.A. Skulls akan mengganti sistem di dalam ponsel dan menyebabkan icon menu utama berubah menjadi gambar tengkorak.
Tidak hanya gambar yang diubah, Skulls juga akan melumpuhkan aplikasi yang icon-nya tadi diubah. Jadi pada saat kita memencet icon dari aplikasi tersebut, maka akan muncul pesan sistem error. Terdapat tiga jenis skulls yaitu Skulls A, Skulls C, dan Skulls H. Cara mencegah virus ini adalah dengan menolak meng-install aplikasi ini dan selalu menutup koneksi Bluetooth saat tidak dibutuhkan.
Salah satu jenis virus Trojan lainnya adalah Doomboot. Virus yang bernama lengkap SymbOS.Doomboot.A. Cara kerja dari virus ini adalah dengan membuat file korup (rusak) dan setelah ponsel terinfeksi maka virus lainnya akan ditempatkan dalam ponsel kita. File yang korup tadi akan membuat ponsel tidak dapat melakukan booting.
Virus Doomboot masuk ke dalam ponsel dengan seakan-akan menyerupai game Doom versi Symbian. Virus ini sangat pandai menyaru, karena setelah ponsel terinfeksi, tidak ada tanda apa pun bahwa ponsel telah terinfeksi virus. Virus ini juga secara otomatis akan menyebar melalui Bluetooth dan mengakibatkan konsumsi baterai ponsel menjadi berlebihan sehingga baterai cepat habis. Doomboot akan membuat ponsel tidak dapat melakukan bootingsaat kita mematikan ponsel dan menyalakan kembali.
Cegah dengan Antivirus CanggihSebagai langkah antisipasi dari virus-virus di atas, Anda perlu meng-install antivirus. Salah satunya Kaspersky Mobile Security. Kaspersky adalah perusahaan antivirus dari Rusia. Awalnya, pada tahun 2004 mereka berhasil mendeteksi dan menghilangkan virus di ponsel bersistem operasi Symbian dan Windows Mobile. Virus yang dapat mereka atasi adalah jenis Trojan dan juga worm.
Dalam menangani virus, Kaspersky akan melakukan scanning terhadap semua file yang masuk ke ponsel. Saat terdeteksi ada virus, ponsel akan langsung berbunyi. Update-nya pun tersedia melalui GPRS. Di samping scanotomatis, Kaspersky juga menyediakan opsi untuk pemindaian virus secara manual.
Selain sebagai antivirus, Kaspersky Mobile Security menyediakan fitur pengamanan data dari pencurian. Melalui Kaspersky, Anda dapat memblokir ponsel dari jarak jauh dan mencari tahu di mana lokasi ponsel Anda.
Untuk menyediakan fasilitas ini, Kaspersky menggabungkan fitur SMS Block, SMS Clean, dan SIM Watch. Fitur SMS block secara otomatis akan memblokir ponsel dengan password yang telah ditentukan sebelumnya. Caranya dengan mengirimkan SMS ke ponsel yang baru hilang. Fitur SMS Clean secara otomatis akan mengosongkan semua isi ponsel dan kartu memori dengan SMS. Kedua fitur ini hanya berfungsi jika SIM Card Anda masih terpasang dan ponsel belum dimatikan oleh sang pencuri.
Jika kebetulan yang mencuri ponsel Anda buru-buru mematikan ponsel begitu dicuri olehnya, dan menggantinya dengan SIM Card lain, maka fitur SMS Watch akan bekerja. Kaspersky secara diam-diam akan mengirimkan SMS dari nomor sang pencuri dan mengirimkannya ke nomor Anda. Selanjutnya, Anda tinggal mengurus kartu baru dengan nomor yang sama, ke operator seluler yang Anda gunakan untuk menerima SMS Watch dari ponsel Anda. Dari data nomor telepon yang didapat, Anda bisa melacak di mana lokasi sang pencuri.
Selain itu, Anda dapat memanfaatkan Kaspersky sebagai penangkal spam. Seperti kita ketahui, sampa saat ini ponsel baru bisa memblokir telepon saja, tidak untuk SMS dan MMS. Nah, di sini Kaspersky menyediakan solusi untuk menangkal spam yang masuk melalui SMS dan MMS.
Yang unik, aplikasi ini juga bisa menyediakan firewall bagi ponsel Anda. Jadi Anda tak perlu khawatir akan terkena virus, saat mengakses internet dari ponsel.
Untuk meng-install aplikasi antivirus ke ponsel, unduh Kaspersky (kmsecurity_wm_sp_7.0.1.37_en.cab/sis, 508KB) dari situs http://www.kaspersky.com/productupdates?chapter=207716169. Setelah itu, pilih jenis sistem operasi, dan bahasa yang ingin Anda instalasikan, lalu salin file tersebut ke memori ponsel. (Sinyal)
Aktifasi GPRS Kartu AS / SIMPATI
GPRS adalah general pocket radio service, salah satu fitur data transfer dari penyedia jaringan seluler yang memungkinkan anda untuk berselancar di dunia maya tanpa harus menggunakan kabel dan alat piranti keras lainnya. Cukup dengan telepon selular yang anda miliki anda bisa langsung terkoneksi ke dunia maya dengan melakukan setting pengaktifan terlebih dahulu tentunya.
Syarat Pengaktifan dan Penggunaan GPRS - Menggunakan handset / hp yang bisa gprs - Ada software browser html / wap pada ponsel anda atau di koputer pc atau laptop jika anda menyambungkannya ke komputer. - Kartu anda dalam keadaan aktif tidak tenggang atau grace period. - Bagi simpati memiliki sisa pulsa minimal Rp. 500,- - Berada di wilayah yang dijangkau fitur GPRS
A. Langkah / Tahap Aktifasi GPRS pada Kartu Halo
1. Mengirim SMS ke 6616 dengan pesan sebagai berikut :
Ketik : GPRS Keterangan : Dikenakan tarif Rp 250 sekali kirim
2. 2 Kali Mendapatkan SMS Konfirmasi dari Server Telkomsel
Tunggu beberapa saat, anda akan menerima konfirmasi sms bahwa aplikasi gprs anda sedang diproses dan membutuhkan waktu kurang lebih sekitar 48 jam atau dua hari. Setelah gprs aktif pada server, anda akan kembali mendapat notifikasi sms kedua yang menyatakan gprs anda sudah aktif.
3. Lakukan seting gprs di ponsel anda dengan parameter umum : - Connection Name : APN Telkomsel - Data Bearer : GPRS - Access Point Name : telkomsel - Username : wap - Prompt Password : No - Password : wap123 - Authentication : Normal - Gateway IP address : 10.1.89.130 - Homepage : http://wap.telkomsel.com - Connection Security : Off - Session Mode : Permanent
B. Langkah / Tahap Aktifasi GPRS pada Kartu Simpati dan Kartu As
1. Mengirim SMS ke 6616 dengan pesan sebagai berikut :
Ketik : GPRS[spasi]nomor ICCID (Integrated Circuit Card Identification) di belakang sim card simpati anda Contoh : GPRS 6210001234567890 Keterangan : Dikenakan tarif Rp 350 sekali kirim
2. 2 Kali Mendapatkan SMS Konfirmasi dari Server Telkomsel
Tunggu beberapa saat, anda akan menerima konfirmasi sms bahwa aplikasi gprs anda sedang diproses dan membutuhkan waktu kurang lebih sekitar 48 jam atau dua hari. Setelah gprs aktif pada server, anda akan kembali mendapat notifikasi sms kedua yang menyatakan gprs anda sudah aktif.
3. Lakukan seting gprs di ponsel anda dengan parameter umum : - Connection Name : APN Telkomsel - Data Bearer : GPRS - Access Point Name : telkomsel - Username : wap - Prompt Password : No - Password : wap123 - Authentication : Normal - Gateway IP address : 10.1.89.130 - Homepage : http://wap.telkomsel.com - Connection Security : Off - Session Mode : Permanent
Selamat mencoba dan semoga berhasil